How the U.S. Accidentally Cracked $15B Worth of Bitcoin Private Keys
In October 2025, the U.S. District Court for the Eastern District of New York revealed an unprecedented crypto asset seizure: the U.S. government confiscated 127,271 Bitcoins, worth about $15 billion at market value.
Shenyu, co-founder of Cobo, clarified that law enforcement did not obtain the private keys through brute-force cracking or hacking, but by exploiting randomness vulnerabilities. Some forums allege authorities directly seized wallet mnemonic phrases or private key files from servers and hardware wallets controlled by Prince Group executive Chen Zhi and his family, but authorities have not publicly disclosed the specifics.
The U.S. Marshals Service subsequently moved these hardware wallets to multi-signature cold storage under the Department of the Treasury. The 9,757 BTC transferred by USMS to an official custodial address on October 15, 2025, originated from this source. In its indictment, the U.S. Department of Justice described Lubian as part of the Prince Group’s Cambodian money laundering network, highlighting the group’s attempt to launder fraudulent funds through “new coins” mined from pools.
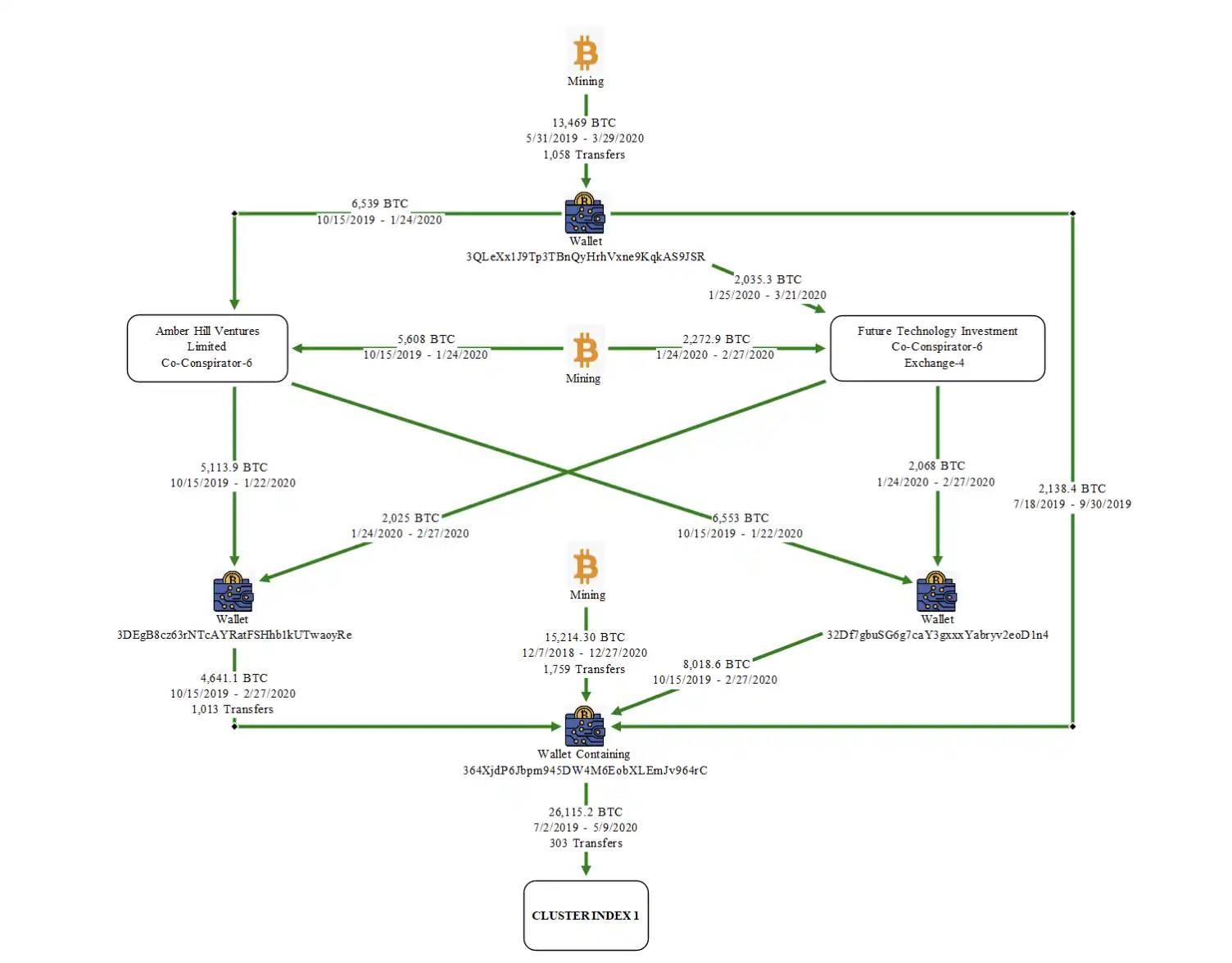
On-chain data tracked by community members indicates these Bitcoins were stolen from Lubian mining pool due to vulnerabilities at the end of 2020. Lubian emerged suddenly that year, with no published team information or operating model, yet its hash rate quickly climbed into the world’s top 10, at one point representing almost 6% of global mining power.
The report notes Chen Zhi boasted to other Prince Group members about “substantial profits because there are no costs.” It’s unclear whether he founded or later acquired control, but the case has brought this dormant whale back into focus, prompting a fresh look at the private key security catastrophe that struck wallets around 2020.
Researchers later discovered the first mnemonic from the faulty key generation process began with “Milk Sad,” leading the incident to be named the Milk Sad event.
Risks Lurking in Weak Randomness
All of this traces back to the Mersenne Twister MT19937-32, a pseudo-random number generator.
Bitcoin private keys should be generated from 256-bit random numbers, resulting in a theoretical 2^256 combinations. Achieving an identical sequence would require 256 perfect coin tosses—a probability so infinitesimal that wallet security depends on the enormity of the possibility space, not chance.
However, the Mersenne Twister MT19937-32 generator used by Lubian and similar tools isn’t a truly fair “coin toss machine” but a flawed device, selecting numbers within a limited and predictable range.
Once hackers understood this pattern, they could rapidly enumerate all possible weak private keys by brute force, unlocking the corresponding Bitcoin wallets.
Due to user misunderstandings about security, from 2019 to 2020, many Bitcoin wallets generated with this “weak random algorithm” amassed enormous wealth, with substantial funds pouring into this vulnerable zone.
Milk Sad team statistics show that between 2019 and 2020, these weak-key wallets held over 53,500 Bitcoins at their peak.
Funds came from both whale-level transfers—like four weak wallets receiving about 24,999 Bitcoins in April 2019—and routine mining rewards, with certain addresses tagged as “lubian.com” receiving over 14,000 Bitcoins within a year. To date, 220,000 such wallets have been identified, with holders apparently unaware of private key generation risks, continuing to funnel assets into them even now.
The Mass Exodus at the End of 2020
This longstanding vulnerability erupted in late 2020. On December 28, 2020, abnormal transactions appeared on-chain: wallets in the Lubian weak key range were emptied within hours, with about 136,951 Bitcoins transferred at once—worth approximately $3.7 billion at the then price of $26,000 per Bitcoin.
Transaction fees were fixed at 75,000 sats regardless of amount, indicating the operator’s deep expertise with Bitcoin network operations. Some funds were distributed as future mining rewards to the Lubian mining pool, showing not all assets ended up with hackers. Nonetheless, victims suffered tangible losses.
Strangely, some transactions included messages like “To the white hat who saved our assets, please contact 1228btc@gmail.com.” Because weak private key addresses were exposed, anyone could send messages to them, and these may not have come from actual victims.
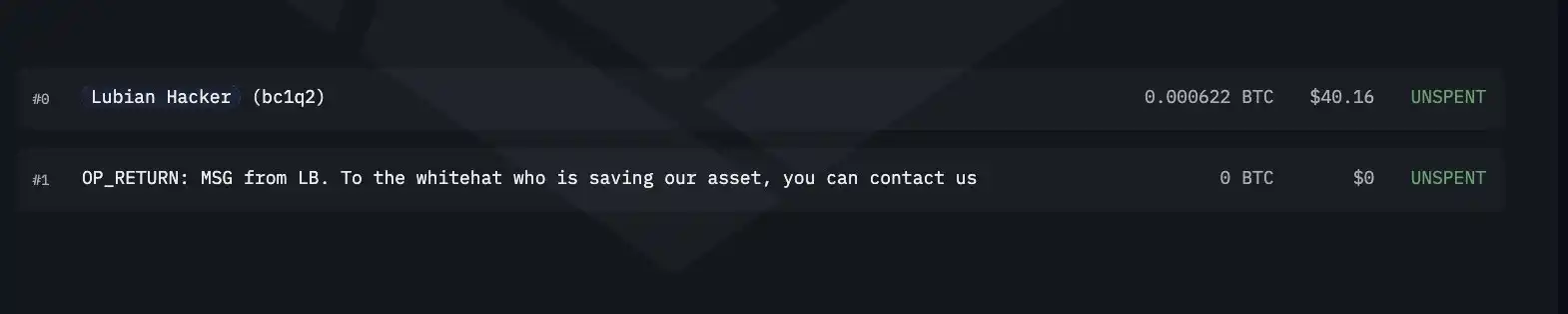
Whether this was hacker taunting or victims seeking help remains unknown. Crucially, this massive transfer was not immediately flagged as theft.
Milk Sad researchers later admitted that, with Bitcoin prices surging and mining pool rewards halted, they were unsure whether the transfers were executed by hackers or Lubian management selling at the peak and restructuring wallets. They noted, “If theft occurred in 2020, it would predate the confirmed Mersenne Twister weak key attack timeline, but we cannot rule it out.”
Due to this uncertainty, the end-of-2020 exodus did not trigger a sector-wide alarm. The vast Bitcoin sum remained dormant on-chain for years, leaving the case unresolved.
The fallout extended beyond Lubian to older Trust Wallet versions. On November 17, 2022, Ledger Donjon security researchers first disclosed the Trust Wallet random number vulnerability to Binance. The project responded quickly, pushing a fix to GitHub the next day and gradually notifying affected users.
Yet, Trust Wallet did not officially reveal vulnerability details or compensation until April 22, 2023. During this delay, hackers exploited the flaw multiple times, including the theft of roughly 50 Bitcoins on January 11, 2023.
Delayed Warning
Meanwhile, another project was developing its own vulnerability.
Libbitcoin Explorer 3.x’s bx seed command used the MT19937 pseudo-random number algorithm with a 32-bit system time as its seed, resulting in a mere 2^32 possible combinations.
Hackers soon launched exploratory attacks, and from May 2023, multiple minor thefts appeared on-chain. On July 12, attacks peaked as bx-generated wallets were swept clean. On July 21, Milk Sad researchers, while investigating user losses, identified the weak randomness in bx seed as the root cause, enabling brute-force private key enumeration. They immediately notified the Libbitcoin team.
Because the command was officially classified as a test tool, initial communications proved challenging. The team ultimately bypassed the project, publicly disclosed the vulnerability, and applied for a CVE ID on August 8.
It was this 2023 discovery that led the Milk Sad team to reverse-engineer historical data. They were stunned to find the weak key space that had accumulated massive funds from 2019 to 2020 was linked to Lubian, and the huge transfer on December 28, 2020, matched the previously described event.
At that time, about 136,951 Bitcoins were held in these weak wallets, with that day’s mass transfer valued at roughly $3.7 billion. The last known on-chain activity was a wallet consolidation in July 2024.
In other words, the suspicious nature of the Lubian incident only surfaced after the weak randomness vulnerability became public. The opportunity for a timely warning was missed, and the whereabouts of the Bitcoins remains unknown. Five years later, only with the joint prosecution by the U.S. Department of Justice (DOJ) and U.K. authorities against the Prince Group and Chen Zhi did new details emerge.
Now, for the community, the maxim “Not your wallet, not your money” depends on the essential guarantee of true randomness.
Statement:
- This article is republished from [BlockBeats], with copyright held by the original author [BUBBLE]. For republication objections, please contact the Gate Learn team, which will process requests per established procedures.
- Disclaimer: The views and opinions expressed are solely those of the author and do not constitute investment advice.
- Other language versions are translated by the Gate Learn team. Without mention of Gate, reproduction, distribution, or plagiarism of translated articles is prohibited.
Related Articles

The Future of Cross-Chain Bridges: Full-Chain Interoperability Becomes Inevitable, Liquidity Bridges Will Decline

Solana Need L2s And Appchains?

Sui: How are users leveraging its speed, security, & scalability?

Navigating the Zero Knowledge Landscape

What is Tronscan and How Can You Use it in 2025?
